Programming & Data Structure
Consider a hash table of size 10 with indices {0, 1,..., 9}, with the hash function h(x) = 3x (mod 10), where linear probing is used to handle collisions. The hash table is initially empty and then the following sequence of keys is inserted into the hash table: 1, 4, 5, 6, 14, 15. The indices where the keys 14 and 15 are stored are, respectively
Consider the following Python declarations of two lists. A = [1, 2, 3] B = [4, 5, 6] Which one of the following statements results in A = [1, 2, 3, 4, 5, 6]?
Consider the following C program: #include stdio.h int main(){ int a = 6 int b = 0; while(a 10) { a = a / 12 + 1; a += b; } printf("%d", a); return 0; } Which one of the following statements is CORRECT?
Consider the following C program: #include stdio.h void fX(); int main(){ fX(); return 0; } void fX(){ char a; if((a=getchar()) != '\n') fX(); if(a != '\n') putchar(a); } Assume that the input to the program from the command line is 1234 followed bya newline character. Which one of the following statements is CORRECT?
Which one of the following sequences when stored in an array at locations A[1],...,A[10] forms a max-heap?
Let SLLdel be a function that deletes a node in a singly-linked list given a pointer to the node and a pointer to the head of the list. Similarly, let DLLdel be another function that deletes a node in a doubly-linked list given a pointer to the node and a pointer to the head of the list. Let n denote the number of nodes in each of the linked lists. Which one of the following choices is TRUE about the worst-case time complexity of SLLdel and DLLdel?
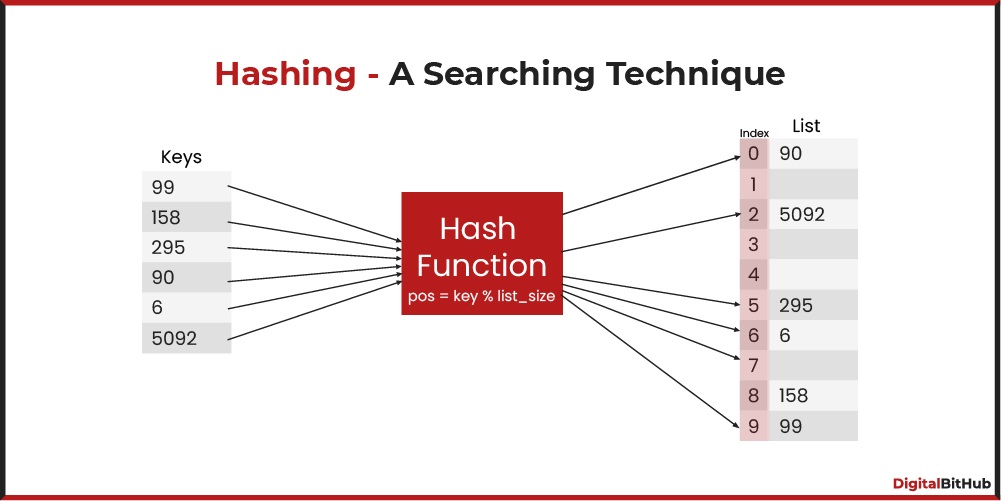
An algorithm has to store several keys generated by an adversary in a hash table. The adversary is malicious who tries to maximize the number of collisions. Let k be the number of keys, m be the number of slots in the hash table, and km. Which one of the following is the best hashing strategy to counteract the adversary?
Suppose we are given n keys, m hash table slots, and two simple uniform hash functions h1 and h2. Further suppose our hashing scheme uses h1 for the odd keys and h2 for the even keys. What is the expected number of keys in a slot?
What is printed by the following ANSI C program? #includestdio.hint main(int argc, char *argv[]){ int x = 1, z[2] = {10, 11}; int *p = NULL; p = x; *p = 10; p = z[1]; *(z[0] + 1) += 3; printf("%d, %d, %d\n", x, z[0], z[1]); return 0;}
Suppose a binary search tree with 1000 distinct elements is also a complete binary tree. The tree is stored using the array representation of binary heap trees. Assuming that the array indices start with 0, the 3rd largest element of the tree is stored at index_____________.
Consider the queues Q1 containing four elements and Q2 containing none (shown as the Initial State in the figure). The only operations allowed on these two queues are Enqueue(Q, element) and Dequeue(Q). The minimum number of Enqueue operations on Q1 required to place the elements of Q1 in Q2 in reverse order (shown as the Final State in the figure) without using any additional storage is___________.
The preorder traversal of a binary search tree is 15, 10, 12, 11, 20, 18, 16, 19. Which one of the following is the postorder traversal of the tree?
What is the worst case time complexity of inserting n elements into an AVL-tree with n elements initially?
Consider the following C program. #include int main () { int a[4] [5] = {{1, 2, 3, 4, 5}, {6, 7,8, 9, 10}, {11, 12, 13, 14, 15}, {16, 17,18, 19, 20}}; printf("%d\n", *(*(a+**a+2)+3)); return(0); } The output of the program is _______.
Consider a double hashing scheme in which the primary hash function is h1(k)=k mod 23, and the secondary hash function is h2(k) = 1 + (k mod 19). Assume that the table size is 23. Then the address returned by probe 1 in the probe sequence (assume that the probe sequence begins at probe I) for key value k = 90 is ______.
In a balanced binary search tree with n elements, what is the worst-case time complexity of reporting all elements in the range [a,b]? Assume that the number of reported elements is k.
Consider the following C functions. int fun1 (int n) { static int i = 0; if (n 0) { ++i; fun1 (n-1); } return (i);} int fun2 (int n) { static int i = 0; if (n 0) { i = i + fun1 (n); fun2 (n-1); } return (i);} The return value of fun2(5) is _____.
Consider the following C functions. int tob (int b, int* arr){ int i; for (i=0; b0; i++) { if (b%2) arr[i]=1; elsearr[i]=0; b = b/2; } return (i);} int pp(int a, int b) { int arr[20]; int i, tot = 1, ex, len; ex = a; len = tob(b, arr); for (i = 0; i len; i++) { if(arr[i] == 1) tot = tot * ex; ex = ex * ex; } return (tot);} The value returned by pp(3,4) is ______.